Authors:
Brian Taylor, Kirk Goldman, Manda Miller, Ted Clark, Kristen Chung, Bella Sunthornpong, Sam Champagne
Abstract:
A methodology for detecting the sale of potentially stolen items on third-party marketplaces by using web scrapers and an algorithm to find similar images to items in stolen items and patterns of behavior indicating theft.
Background:
Finding and detecting items that have been stolen due to organized retail crime is difficult. Today, the method for finding stolen items is very manual and is not proactive. Individuals would need to comb through stolen item databases and see if they are able to find postings that might correlate. Current methods do not monitor third-party marketplaces for patterns of suspicious posting behavior. Lastly, current methods do not incorporate geographic location as a basis for finding stolen items.
Description:
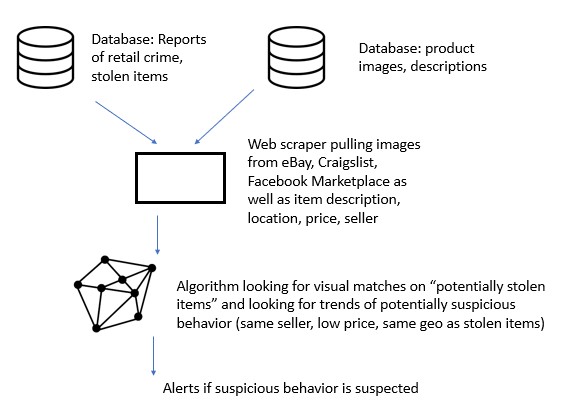
Part 1: Database of stolen items that includes item description/date stolen/location of store
Part 2: Image database stolen items
Part 3: Use web scraper to pull items that match stolen items.
Part 4: Algorithm to match similarity of “potentially stolen item” to image database of stolen item
Part 5: Compare location of “potentially stolen item” to database of stolen items
Part 6: Alert for patterns of suspicious behaviors (ex- same seller/large number of flagged items, same item/same geo as theft/large number, same item/unusually low price)
Features:
- Retailer search for stolen items
- Law enforcement search for criminal behavior
- Manufacturer search for stolen items
Claims:
- Geographic search for stolen items
- Ability to find similar images matching stolen items
- Ability to alert and detect for suspicious posting behavior
Supporting Art:
- Item databases of stolen items
- Algorithm based on suspicious posting behavior, geography
- Web scraper
- Image similarity algorithm
TGCS Reference 4118









